What is a web application firewall (WAF)?
By monitoring and filtering HTTP traffic between a web application and the internet, online applications.
Read our Web Application Firewall (WAF) Buyer’s Guide for more information (Updated: September 2022).
Cross-site scripting (XSS), cross-site forgery, SQL injection, cookie poisoning, file inclusion, and other application layer attacks are all prevented by a WAF. With a WAF in place, you can thwart attempts to compromise your systems to steal data from your firm. WAFs are not made to withstand all kinds of assaults. Instead, a WAF is often used with tools to develop a comprehensive security strategy against various attack vectors.
How does it work:
The Hypertext Transfer Protocol (HTTP) requests are analyzed by a WAF, which then applies a set of rules to distinguish between legitimate and malicious HTTP requests. A WAF examines GET and POST requests are significant components of HTTP dialogues. to modify their state, whereas GET requests are used to get data from the server.
Key benefits of a web application firewall:
Any online business needing to handle sensitive customer data securely might benefit significantly from a WAF. To protect their online applications from sophisticated and targeted assaults like cross-site scripting (XSS) and SQL injection that could lead to fraud or data theft, businesses often employ a WAF. These intrusions can seriously undermine consumer confidence and possibly bring about legal repercussions when practical. A WAF’s additional security can assist defend a business’s standing in the marketplace and reputation.
The administrative effort of making sure that web application security testing is conducted regularly is also lessened by a WAF. Application security teams may monitor what should and shouldn’t be allowed through a WAF by actively setting rules and guidelines. Teams can promptly inform of an attack that is already underway so they can react to possible security incidents much faster.
Here is our list of the best web application firewalls:
- WAF for Imperva Cloud Imperva WAF Gateway is a cloud-based web application firewall with an on-premises comparable appliance.
- Web Application Firewall by Barracuda This WAF also offers vulnerability detection and data loss protection and is available as a SaaS solution, a private cloud, an appliance, or a VM.
- Customizable, all-in-one Multi/Hybrid/Private/SaaS/Kubernetes-based WAF with Bot Protection, RASP, DDoS, and CDN solution is Prophaze Web Application Firewall. Rapid onboarding, limitless SSL Certs, and round-the-clock assistance.
- Protect with F5 Essential App, a cloud-based WAF that is simple to set up and operate and is designed for non-technical users.
- DDoS defense can be added to Cloudflare WAF, a cloud-based security program.
- Akamai Kona Site Defender combines off-site WAF and DDoS protection.
- Sucuri Website Firewall (LEARN MORE) Comprises DDoS defense and is a component of a package of off-site application security services.
- Fortinet FortiWeb A bundle of edge services that includes a load balancer, an SSL off-loader, and a web application firewall in a cloud service, appliance, or virtual machine.
What WAF limitations do I need to be aware of?
A specialized type of firewall called a WAF is made to guard online applications and your company against being the target of skimming attacks. WAFs are placed in front of web applications to identify and stop harmful or unauthorized behavior to analyze web traffic. A WAF acts as an enforcement point for security policies and is positioned between a web application and the client endpoint by the Payment Card Industry Data Security Standards (PCI-DSS). Web application firewalls defend against threats, including SQL injection, file inclusion, cross-site scripting (XSS), and cross-site forgery.
WAFs cannot protect businesses or their customers from:
Sophisticated malware for skimming: Businesses cannot be shielded from more advanced skimming malware by WAFs.
Attacks using the supply chain and drive-by skimming: Data exfiltration or modified JavaScript code cannot be detected by WAFs.
Attacks Using Sideloading and Chainloading: WAFs cannot defend against the skimming that sideloaded JavaScript code performs.
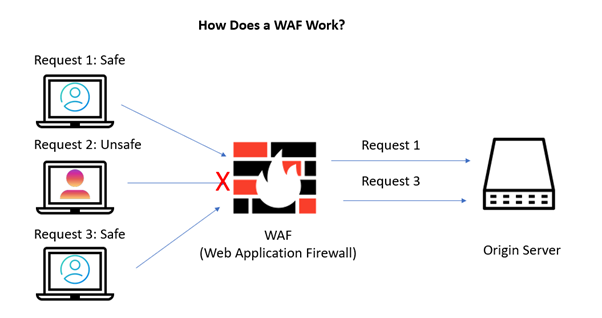
How does a Web Application Firewall work?
The “policies” or “security policies” that drive a WAF’s operation are a preprogrammed set of security regulations. These policies determine the kinds of data packets that can transit through it. A WAF then analyzes the HTTP requests and application traffic. The application layer blocks harmful inbound communication from passing through.
The GET and POST requests are the two primary components of an HTTP conversation that WAF technology watch to modify its state, whereas GET requests are used to get data from the server.
Improve Your Cybersecurity with Web Application Firewall Solutions: 
Cybersecurity dangers are diversified and complicated and appear to be here to stay. Nevertheless, having the appropriate web application firewall solution will help keep your website secure from hackers. By doing this, you also secure your brand’s reputation with customers, who should always be able to rely on your website to protect their private information.
Filter traffic to and from your website by investing in a better cybersecurity approach. The assurance that your website and users are secure against cybercriminals is priceless in the end.