A botnet is a coordinated network of internet-connected devices used for malevolent purposes. A bot is a computer that is part of a botnet. Bots are also known as “zombie computers” because of their capacity to work without the knowledge of their owners.
These are botnets, or networks of remote-controlled computers.
Malware has infiltrated these machines, allowing them to be controlled remotely.
Botnets can range in size from hundreds of thousands to millions of computers. It has evolved into one of the most serious threats to today’s security systems. Botnet is a combination of the terms “robot” and “network.”
Botnets are, in a broad sense, a network of robots that are used to execute cybercrime. Botmasters or bot herders are the cybercriminals in charge of them. Botnets can be used to launch a distributed denial-of-service (DDoS) attack, steal data, send spam, and get access to the device and its connection.
The botnet’s owner can use command and control (C&C) software to manage it.
Botnets are an example of good technology being used for negative purposes.
Botnets that are illegal and malicious should be avoided. When botnets gain access to your computer through malicious software.
Botnets were designed primarily as a tool for legitimate reasons in Internet relay chat (IRC) channels. Hackers eventually exploited the flaws in IRC networks and created bots to undertake nefarious actions like password stealing, keystroke logging, and so on. Botnets are also becoming a more common topic of conversation in the cybersecurity community.
These aren’t usually designed to infect a single computer; instead, they’re made to infect millions of them. Botherders frequently use a trojan horse, or virus, to install botnets on computers.
Botnets are notoriously difficult to spot. A botnet builder can create a central command and control server using methods and tools that can be accessed online in minutes, and then employ social engineering to implant malware onto the victim’s machine.
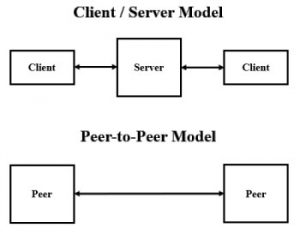
Architecture of Botnet
In essence, bot programmes are built as clients that communicate with existing servers. This allows the bot herder (the person in charge of the botnet) to handle everything from afar, obscuring their traffic. Many contemporary botnets now communicate over existing peer-to-peer networks.
- Client-server botnet structure- A client-server botnet is built up like a basic network, with one primary server overseeing the transfer of data from each client. For gaining and retaining control of the botnet, the client-server paradigm works well.
- Peer-to-peer (P2P) botnets are newer botnets that use a more interconnected peer-to-peer (P2P) structure. Each infected device in a P2P botnet serves as both a client and a server. The structure of P2P botnets makes it more difficult for law authorities to locate any centralised source.
Is Installing Botnet Is Illegal
It is illegal to install malware on a victim’s computer without their agreement in order to construct a botnet, and the botnet’s activity may be criminal.